Welcome to our exciting journey into the world of ethical hacking! In this blog, we’ll explore the top best ethical hacking tools that are making waves globally. Whether you’re a cyber security enthusiast, a professional ethical hacker, or simply curious about the tools shaping our digital defence landscape, you’re in the right place. Join us as we delve into the cutting-edge software and utilities empowering security professionals to safeguard digital systems, uncover vulnerabilities, and fortify against cyber threats. Let’s embark on this exploration together and discover the arsenal of tools at the forefront of ethical hacking prowess.
Zenmap

In today’s digitally interconnected world, the importance of cybersecurity cannot be overstated. Ethical hacking, also known as penetration testing, involves systematically probing for vulnerabilities in a system or network to preemptively address potential security breaches. Ethical hackers utilize a variety of tools to simulate cyber attacks and assess the robustness of an organization’s defenses. One such tool that has gained prominence is Zenmap.
What is Zenmap? – Best Ethical Hacking Tools
Zenmap is the graphical user interface (GUI) for the renowned network scanning tool Nmap (Network Mapper). Nmap itself is a powerful open-source utility designed for network exploration and security auditing. Zenmap provides users with an intuitive interface to interact with Nmap’s extensive functionality, making it accessible to both novice and experienced users.
Upon launching Zenmap, users are greeted with a user-friendly interface that simplifies the process of network scanning and analysis. The interface is divided into distinct sections, including target selection, scan options, and results display. Navigating through Zenmap is straightforward, with comprehensive tooltips guiding users through each step of the scanning process.
Zenmap supports a myriad of scanning techniques, ranging from simple ping scans to complex vulnerability detection scans. Users can choose from various scan types based on their specific requirements, such as TCP connect scans, UDP scans, and SYN scans. Additionally, Zenmap allows for the customization of scan parameters, enabling users to fine-tune their scans for optimal results.
One of the standout features of Zenmap is its support for Nmap scripts, which extend the tool’s functionality beyond traditional scanning. Nmap scripts, written in the Lua programming language, enable users to automate repetitive tasks, perform advanced vulnerability detection, and gather detailed information about target systems. By leveraging Nmap scripts, ethical hackers can enhance the efficacy of their scans and uncover hidden vulnerabilities.
Zenmap in Penetration Testing
Ethical hackers rely on Zenmap as a fundamental tool in their arsenal for conducting penetration tests. By utilizing Zenmap’s comprehensive scanning capabilities, penetration testers can identify potential entry points into a network, assess the effectiveness of existing security measures, and recommend remedial actions to bolster defenses. Moreover, Zenmap’s compatibility with Nmap scripts facilitates in-depth analysis and exploitation of vulnerabilities, thereby facilitating thorough security assessments.
Security Risks and Ethical Considerations
While Zenmap empowers ethical hackers to safeguard systems against cyber threats, its misuse can pose ethical and legal risks. It is imperative for users to adhere to ethical guidelines and legal regulations governing the use of penetration testing tools. Unauthorized scanning of networks or systems without explicit permission can result in severe repercussions, including legal action and damage to reputation. Ethical hackers must exercise caution and transparency in their actions to ensure responsible and lawful conduct.
Zenmap vs. Other Ethical Hacking Tools
In comparison to other ethical hacking tools, Zenmap offers several distinct advantages. Its intuitive GUI makes it accessible to users of all skill levels, while its integration with Nmap provides unparalleled scanning capabilities. Additionally, Zenmap’s support for Nmap scripts enhances its versatility, allowing for advanced customization and automation of scans. While other tools may excel in specific areas, Zenmap’s comprehensive feature set makes it a preferred choice for many ethical hackers.
Case Studies and Success Stories
Numerous real-world examples attest to Zenmap’s effectiveness in identifying and mitigating security vulnerabilities. From small businesses to multinational corporations, organizations across various industries have leveraged Zenmap to fortify their defenses and safeguard critical assets. Whether it’s uncovering misconfigured servers, identifying outdated software, or detecting unauthorized devices on a network, Zenmap has consistently proven its value in enhancing cybersecurity posture.
Getting Started with Zenmap
For those looking to harness the power of Zenmap for ethical hacking purposes, getting started is relatively straightforward. The tool is freely available for download on the official Nmap website, with installation packages tailored for different operating systems. Additionally, comprehensive documentation and tutorials are available to assist users in familiarizing themselves with Zenmap’s features and functionalities. By investing time in learning and mastering Zenmap, aspiring ethical hackers can embark on a rewarding journey towards bolstering cybersecurity defenses.
Read About: Top Best Rich Man All Time In The World
Angry IP Scanner – Best Ethical Hacking Tools

In the realm of cybersecurity, ethical hacking plays a crucial role in identifying vulnerabilities within systems and networks before malicious actors exploit them. Ethical hackers, also known as white-hat hackers, utilize various tools to assess and improve the security posture of organizations.
Angry IP Scanner: An Overview
Angry IP Scanner stands as a powerful and versatile open-source tool used for network scanning. It allows users to scan IP addresses and ports quickly and efficiently, providing valuable insights into the network’s structure and potential vulnerabilities.
The primary purpose of Angry IP Scanner is to facilitate network reconnaissance, aiding in the identification of active hosts, their respective IP addresses, and open ports. This information is instrumental in assessing the security of a network and detecting any potential threats or weaknesses.
Features of Angry IP Scanner
Angry IP Scanner excels in scanning large ranges of IP addresses swiftly, providing comprehensive results in a matter of seconds. Its multi-threaded approach ensures optimal performance, making it suitable for both small-scale and enterprise-level environments.
With its robust port scanning capabilities, Angry IP Scanner enables users to identify open ports on target hosts. This feature is vital for detecting services running on specific ports and assessing their security configurations.
One of the standout features of Angry IP Scanner is its extensive customization options, allowing users to tailor the scanning process according to their specific requirements. From defining scan ranges to configuring timeout settings, users have full control over the scanning parameters.
How to Use Angry IP Scanner
Angry IP Scanner boasts a straightforward installation process across various operating systems, including Windows, macOS, and Linux. Users can download the application from the official website and install it with minimal effort.
Once installed, using Angry IP Scanner is intuitive and user-friendly. Users simply need to specify the target IP range, select the desired scanning options, and initiate the scan. The results are presented in a clear and concise manner, allowing for easy interpretation.
Advantages of Using Angry IP Scanner
Angry IP Scanner’s versatility makes it suitable for a wide range of use cases, including network troubleshooting, security auditing, and system administration. Its lightweight nature and minimal resource requirements ensure optimal performance across various environments.
Despite its advanced capabilities, Angry IP Scanner features a simple and intuitive interface, making it accessible to users with varying levels of technical expertise. The straightforward layout and intuitive controls streamline the scanning process, minimizing the learning curve.
Angry IP Scanner’s speed and efficiency set it apart from other network scanning tools. Its multi-threaded scanning engine allows for rapid scanning of large IP ranges without compromising accuracy, making it ideal for time-sensitive tasks.
Ethical Implications of Using Angry IP Scanner
While Angry IP Scanner is designed for ethical purposes, it’s essential for users to adhere to legal and regulatory guidelines when conducting network scans. Unauthorized scanning of networks without proper authorization can lead to legal repercussions.
Ethical hackers must exercise caution and discretion when using Angry IP Scanner to avoid causing disruptions or violating the privacy of others. Responsible usage entails obtaining proper authorization before scanning networks and respecting the boundaries of ethical hacking.
Comparison with Other Ethical Hacking Tools
Angry IP Scanner stands out among its peers due to its simplicity, speed, and versatility. However, it’s essential to compare it with other popular tools such as Nmap and Wireshark to understand its strengths and limitations fully.
Real-World Applications
Angry IP Scanner is widely used in network security auditing to identify vulnerabilities and assess the overall security posture of an organization’s network infrastructure. Its comprehensive scanning capabilities provide valuable insights for security professionals.
System administrators leverage Angry IP Scanner to monitor network activity, troubleshoot connectivity issues, and identify rogue devices on the network. Its ease of use and efficiency make it an indispensable tool for maintaining network integrity.
Limitations of Angry IP Scanner
While Angry IP Scanner excels in basic network scanning tasks, it may lack some advanced features found in other commercial tools. Organizations with specific requirements may need to supplement it with additional software.
Angry IP Scanner’s compatibility with certain network configurations and environments may vary, leading to potential issues during the scanning process. Users should thoroughly test the tool in their respective environments to ensure optimal performance.
Best Practices for Ethical Hacking with Angry IP Scanner
Keeping Angry IP Scanner updated with the latest patches and security fixes is crucial for maintaining its effectiveness and security. Regular updates ensure compatibility with new technologies and mitigate potential vulnerabilities.
Ethical hackers should document their findings meticulously and prepare detailed reports summarizing the results of their scans. This documentation helps organizations understand their security posture better and prioritize remediation efforts.
Case Studies
Numerous organizations have successfully implemented Angry IP Scanner as part of their security toolkit, enabling them to identify and address vulnerabilities proactively. Case studies highlighting these success stories serve as testimonials to the tool’s efficacy.
Read About: Top Best Airports All Time In The World
Advanced IP Scanner

Ethical hacking stands as a crucial practice in the cybersecurity domain, focusing on identifying vulnerabilities within systems and networks to enhance their security. Central to this practice are ethical hacking tools, which empower security professionals to assess and fortify digital infrastructures against potential threats.
Advanced IP Scanner: An Overview – Best Ethical Hacking Tools
Advanced IP Scanner represents a powerful and user-friendly tool designed for network scanning and analysis. Developed by Famatech, this free software facilitates the detection of devices connected to a network, providing essential information such as IP addresses, MAC addresses, and open ports.
The primary purpose of Advanced IP Scanner is to enable users to explore their local area networks (LANs) comprehensively. By scanning IP addresses and identifying active hosts, Advanced IP Scanner aids in network management, troubleshooting, and security assessment.
Features of Advanced IP Scanner
Advanced IP Scanner excels in scanning IP addresses within a specified range, offering real-time insights into the devices connected to a network. Its fast and efficient scanning engine ensures quick results, making it an invaluable tool for network administrators and security professionals.
With its built-in port scanning capabilities, Advanced IP Scanner allows users to detect open ports on target devices. This feature is instrumental in identifying potential vulnerabilities and assessing the security posture of networked systems.
Advanced IP Scanner offers remote control functionality, enabling users to access and manage networked devices remotely. This feature streamlines administrative tasks and facilitates efficient remote troubleshooting, enhancing overall network efficiency and productivity.
How to Use Advanced IP Scanner
Installing Advanced IP Scanner is a straightforward process, requiring users to download the software from the official website and follow the on-screen instructions. The software is available for Windows operating systems and is compatible with both 32-bit and 64-bit versions.
Upon installation, users can launch Advanced IP Scanner and initiate a scan by specifying the IP address range of their network. The software will then scan the specified range and display the results in a user-friendly interface, allowing users to view detailed information about each detected device.
Advantages of Using Advanced IP Scanner
One of the key advantages of Advanced IP Scanner is its intuitive user interface, which makes it accessible to users with varying levels of technical expertise. The software’s user-friendly design streamlines the scanning process, allowing users to navigate effortlessly and obtain the information they need quickly.
Advanced IP Scanner provides comprehensive network analysis capabilities, allowing users to gain valuable insights into their network infrastructure. From identifying active hosts to detecting open ports, the software offers a wealth of information essential for effective network management and security assessment.
The remote administration features of Advanced IP Scanner empower users to manage networked devices efficiently from a central location. Whether performing software updates, troubleshooting connectivity issues, or accessing files remotely, the software simplifies the task of network administration.
Ethical Implications of Using Advanced IP Scanner
While Advanced IP Scanner is designed for ethical purposes, users must ensure compliance with relevant laws and regulations governing network scanning activities. Unauthorized scanning of networks without proper authorization may constitute a violation of privacy laws and could result in legal repercussions.
Ethical hackers and network administrators must exercise caution and responsibility when using Advanced IP Scanner to avoid infringing upon the rights and privacy of others. Responsible usage entails obtaining proper authorization before conducting network scans and adhering to ethical guidelines and best practices.
Comparison with Other Ethical Hacking Tools
Advanced IP Scanner distinguishes itself from other ethical hacking tools through its simplicity, versatility, and robust feature set. However, it’s essential to compare it with other popular tools such as Angry IP Scanner and Nmap to understand its strengths and limitations fully.
Real-World Applications
Advanced IP Scanner finds widespread application in network management and monitoring, allowing administrators to identify and resolve issues promptly. Whether detecting unauthorized devices or monitoring network traffic, the software enhances the efficiency and security of networked environments.
Security professionals utilize Advanced IP Scanner for security assessment and auditing purposes, identifying vulnerabilities and assessing the overall security posture of an organization’s network infrastructure. The software’s comprehensive scanning capabilities provide valuable insights for mitigating security risks and strengthening defenses.
Limitations of Advanced IP Scanner
Advanced IP Scanner is primarily designed for Windows operating systems and may have limited compatibility with other platforms. Users operating non-Windows environments may need to explore alternative solutions to meet their scanning requirements.
While Advanced IP Scanner offers a wide range of features essential for network scanning and analysis, it may lack some advanced functionalities found in other commercial tools. Organizations with specific requirements may need to supplement it with additional software to address their needs fully.
Best Practices for Ethical Hacking with Advanced IP Scanner
Before conducting network scans with Advanced IP Scanner, users must obtain proper authorization from the relevant stakeholders. This ensures compliance with legal and ethical guidelines and helps prevent unauthorized access to networked systems.
Ethical hackers and security professionals should document their scanning activities meticulously and prepare detailed reports summarizing their findings. This documentation serves as a record of the scanning process and provides valuable insights for remediation efforts and future security enhancements.
Read About: Top Best Largest Cities All Time In The World
Fping – Best Ethical Hacking Tools
Ethical hacking serves as a critical practice in the field of cybersecurity, involving the use of various tools and techniques to identify vulnerabilities within systems and networks. These tools play a pivotal role in strengthening digital defenses and mitigating security risks.
Fping: An Overview
Fping stands as a versatile and efficient network scanning tool designed to assess the reachability of hosts on an Internet Protocol (IP) network. Developed by Roland Schemers, Fping offers enhanced functionality compared to traditional ping utilities, making it an invaluable asset for network administrators and security professionals.
The primary purpose of Fping is to facilitate the rapid and comprehensive scanning of IP addresses within a network. By sending Internet Control Message Protocol (ICMP) echo request packets to target hosts and analyzing their responses, Fping provides valuable insights into network connectivity and device availability.
Features of Fping
Fping distinguishes itself through its ability to perform parallel processing of ping requests, enabling users to scan multiple hosts simultaneously. This feature enhances scanning efficiency and reduces the time required to assess the reachability of hosts within a network.
Fping offers customizable output formats, allowing users to tailor the presentation of scan results according to their preferences. Whether generating concise summaries or detailed reports, the software provides flexibility in displaying ping statistics and diagnostic information.
With its scripting support capabilities, Fping enables users to automate repetitive tasks and integrate ping functionality into their scripts and workflows. This feature enhances productivity and facilitates the seamless integration of Fping into existing network management and security frameworks.
How to Use Fping
Installing Fping is a straightforward process, typically involving the download and installation of the software package from the official website or package repositories. Fping is compatible with various operating systems, including Linux, Windows, and macOS, ensuring broad accessibility for users.
Once installed, using Fping is intuitive and user-friendly. Users can launch the software from the command line interface and specify the target IP addresses or hostnames they wish to scan. Fping will then send ICMP echo request packets to the specified targets and display the corresponding responses.
Advantages of Using Fping
Fping’s parallel processing capabilities enable users to scan large networks quickly and efficiently. By leveraging multiple threads to send ping requests concurrently, Fping significantly reduces the time required to assess the reachability of hosts within a network.
Fping offers flexible output options, allowing users to customize the format and content of scan results to suit their needs. Whether generating simple text-based output or exporting data to other formats, such as CSV or XML, the software provides versatility in presenting ping statistics and analysis.
The scripting and automation capabilities of Fping empower users to automate routine network scanning tasks and integrate ping functionality into their scripts and workflows. This feature enhances efficiency and enables seamless integration with existing network management and security systems.
Ethical Implications of Using Fping
While Fping is intended for legitimate network scanning and diagnostics, users must ensure compliance with relevant laws and regulations governing network security practices. Unauthorized or indiscriminate use of Fping may constitute a violation of privacy laws and could result in legal consequences.
Ethical hackers and network administrators must exercise discretion and responsibility when using Fping to avoid causing disruptions or infringing upon the rights of others. Responsible usage entails obtaining proper authorization before conducting network scans and adhering to ethical guidelines and best practices.
Comparison with Other Ethical Hacking Tools
Fping offers several advantages over traditional ping utilities and other network scanning tools, including enhanced speed, flexibility, and scripting support. However, it’s essential to compare it with other popular tools, such as Nmap and Angry IP Scanner, to understand its strengths and limitations fully.
Real-World Applications
Fping finds widespread application in network troubleshooting and diagnostics, allowing administrators to identify connectivity issues and assess the availability of networked devices. Its fast and comprehensive scanning capabilities streamline the troubleshooting process and facilitate prompt resolution of issues.
Security professionals utilize Fping for security assessment and monitoring purposes, enabling them to detect unauthorized devices and assess the overall security posture of a network. By identifying reachable hosts and analyzing their responses, Fping provides valuable insights for detecting potential vulnerabilities and mitigating security risks.
Limitations of Fping
Fping relies on the ICMP protocol for sending ping requests and receiving responses from target hosts. While ICMP is widely supported by most networked devices, its usage may be restricted or blocked in certain environments, limiting Fping’s effectiveness in such cases.
While Fping excels in basic network scanning tasks, it may lack some advanced features found in other commercial tools. Organizations with specific requirements, such as advanced port scanning or protocol analysis, may need to supplement Fping with additional software to meet their needs fully.
Best Practices for Ethical Hacking with Fping
Before using Fping for network scanning activities, users must obtain proper authorization from the relevant stakeholders. This ensures compliance with legal and ethical guidelines and helps prevent unauthorized access to networked systems.
Ethical hackers and network administrators should exercise discretion and caution when using Fping to avoid causing disruptions or inadvertently disclosing sensitive information. Responsible usage entails respecting the privacy and security of networked systems and adhering to ethical principles at all times.
Read About: Top Best Big Cities All Time In The World
Unicornscan

Ethical hacking is a crucial aspect of cybersecurity, focusing on identifying vulnerabilities within systems and networks to bolster their defenses against potential threats. Ethical hackers leverage a variety of tools and techniques to assess the security posture of organizations and safeguard their digital assets.
Unicornscan: An Overview – Best Ethical Hacking Tools
Unicornscan represents a powerful and feature-rich network reconnaissance tool used for probing networks and identifying active hosts and services. Developed by SecureState, Unicornscan offers advanced scanning capabilities and comprehensive analysis features, making it a valuable asset for security professionals and penetration testers.
The primary purpose of Unicornscan is to provide network administrators and security professionals with insights into the structure and composition of networks. By sending packets to target hosts and analyzing their responses, Unicornscan enables users to map network topologies, identify open ports, and detect potential vulnerabilities.
Features of Unicornscan
Unicornscan offers comprehensive network scanning capabilities, allowing users to perform a variety of scanning techniques, including TCP, UDP, ICMP, and ARP scans. This versatility enables users to gather detailed information about networked devices and services, facilitating effective security assessments.
With its advanced packet crafting capabilities, Unicornscan enables users to customize and manipulate network packets according to their specific requirements. This feature is particularly useful for crafting specialized payloads and conducting targeted attacks against vulnerable systems.
Unicornscan boasts an extensible plugin architecture, allowing users to extend its functionality through custom plugins and scripts. This flexibility enables users to tailor Unicornscan to their unique requirements and integrate it seamlessly into existing security frameworks and workflows.
How to Use Unicornscan
Installing Unicornscan typically involves downloading the software package from the official website or package repositories and following the provided instructions. Unicornscan is compatible with various operating systems, including Linux, Windows, and macOS, ensuring broad accessibility for users.
Once installed, using Unicornscan involves specifying the target IP addresses or ranges and selecting the desired scanning options, such as scan type and port range. Unicornscan will then initiate the scan and provide detailed results, allowing users to analyze network vulnerabilities and devise appropriate remediation strategies.
Advantages of Using Unicornscan
Unicornscan offers advanced scanning techniques and comprehensive analysis features, enabling users to perform in-depth assessments of networked environments. From identifying open ports to detecting potential security misconfigurations, Unicornscan provides valuable insights for enhancing network security.
Unicornscan offers customizable output formats, allowing users to tailor the presentation of scan results according to their preferences. Whether generating simple text-based reports or exporting data to other formats, such as XML or CSV, Unicornscan provides flexibility in analyzing and interpreting scan results.
Unicornscan is highly scalable and performs efficiently even when scanning large networks with numerous hosts and services. Its optimized scanning engine and multi-threaded architecture ensure fast and reliable performance, making it suitable for both small-scale and enterprise-level environments.
Ethical Implications of Using Unicornscan
While Unicornscan is intended for legitimate security testing and network reconnaissance, users must ensure compliance with relevant laws and regulations governing cybersecurity practices. Unauthorized or indiscriminate use of Unicornscan may constitute a violation of privacy laws and could result in legal consequences.
Ethical hackers and security professionals must exercise discretion and responsibility when using Unicornscan to avoid causing disruptions or infringing upon the rights of others. Responsible usage entails obtaining proper authorization before conducting network scans and adhering to ethical guidelines and best practices.
Comparison with Other Ethical Hacking Tools
Unicornscan stands out among its peers due to its advanced scanning capabilities, extensible plugin architecture, and customizable output formats. However, it’s essential to compare it with other popular tools, such as Nmap and Masscan, to understand its strengths and limitations fully.
Real-World Applications
Unicornscan finds widespread application in network mapping and discovery, allowing users to identify active hosts, services, and vulnerabilities within a network. Its comprehensive scanning capabilities and detailed analysis features facilitate effective network reconnaissance and security assessment.
Security professionals utilize Unicornscan for penetration testing and vulnerability assessment purposes, enabling them to identify and exploit security weaknesses in target systems and applications. By simulating real-world attack scenarios, Unicornscan helps organizations strengthen their defenses and mitigate potential risks.
Limitations of Unicornscan
Unicornscan may have a steep learning curve for novice users due to its advanced features and complex scanning techniques. Users may require significant expertise and experience to fully leverage Unicornscan’s capabilities and derive meaningful insights from scan results.
Unicornscan’s comprehensive scanning techniques and advanced analysis features may require substantial computing resources, particularly when scanning large networks or conducting intensive scans. Users should ensure adequate hardware resources to achieve optimal performance and reliability.
Best Practices for Ethical Hacking with Unicornscan
Before using Unicornscan for security testing and network reconnaissance activities, users must obtain proper authorization from the relevant stakeholders. This ensures compliance with legal and ethical guidelines and helps prevent unauthorized access to networked systems.
Ethical hackers and security professionals should exercise caution and discretion when using Unicornscan to avoid causing disruptions or inadvertently disclosing sensitive information. Responsible usage entails respecting the privacy and security of networked systems and adhering to ethical principles at all times.
Read About: Top Best Tech Companies All Time In The World
Netcat – Best Ethical Hacking Tools
Ethical hacking is a vital practice in cybersecurity, involving the use of various tools and techniques to identify vulnerabilities within systems and networks. These tools empower security professionals to assess the security posture of organizations and implement measures to mitigate potential risks.
Netcat: An Overview
Netcat, also known as “nc,” is a versatile networking utility that provides a wide range of functionality related to network connections. Initially developed by Hobbit in 1995, Netcat has since become a staple tool in the arsenal of ethical hackers and network administrators due to its flexibility and power.
The primary purpose of Netcat is to facilitate the creation and manipulation of network connections. It serves as a Swiss Army knife for networking tasks, enabling users to perform tasks such as port scanning, banner grabbing, file transfer, and remote shell access.
Features of Netcat
Netcat allows users to establish various types of network connections, including TCP and UDP connections, as well as UNIX domain sockets. This versatility enables users to communicate with remote hosts and services efficiently.
Netcat can be used for port scanning, enabling users to identify open ports on target hosts. By sending connection requests to specific ports and analyzing the responses, Netcat provides valuable insights into the network topology and potential security vulnerabilities.
Netcat facilitates file transfer between hosts by establishing a network connection and transferring data streams between them. This feature is useful for transferring files securely and efficiently over a network.
How to Use Netcat
Installing Netcat typically involves downloading the software package from the official website or package repositories and following the provided instructions. Netcat is available for various operating systems, including Linux, Windows, and macOS.
Once installed, using Netcat involves specifying the desired command-line options and arguments to perform specific networking tasks. Users can utilize Netcat’s various functionalities, such as connecting to remote hosts, listening for incoming connections, and transferring data streams.
Advantages of Using Netcat
Netcat’s versatility makes it a valuable tool for a wide range of networking tasks, including port scanning, banner grabbing, file transfer, and remote administration. Its flexible command-line interface allows users to customize its behavior according to their specific requirements.
Netcat is known for its efficiency and performance, enabling users to establish network connections quickly and transfer data streams seamlessly. Its lightweight nature and minimal resource requirements make it suitable for use in various environments, from individual workstations to enterprise networks.
Netcat is available for various operating systems, including Linux, Windows, and macOS, ensuring broad compatibility and accessibility for users across different platforms. This cross-platform support makes Netcat an ideal choice for network administrators and security professionals.
Ethical Implications of Using Netcat
While Netcat is a legitimate networking utility, users must ensure compliance with relevant laws and regulations governing cybersecurity practices. Unauthorized or malicious use of Netcat may constitute a violation of privacy laws and could lead to legal consequences.
Ethical hackers and network administrators must exercise discretion and responsibility when using Netcat to avoid causing disruptions or infringing upon the rights of others. Responsible usage entails obtaining proper authorization before performing network-related activities and adhering to ethical guidelines and best practices.
Comparison with Other Ethical Hacking Tools
Netcat stands out among its peers due to its simplicity, versatility, and efficiency. However, it’s essential to compare it with other popular tools, such as Nmap, Wireshark, and Metasploit, to understand its strengths and limitations fully.
Real-World Applications
Netcat finds widespread application in network troubleshooting and diagnostics, allowing users to identify connectivity issues, analyze network traffic, and diagnose network-related problems efficiently.
Security professionals utilize Netcat for penetration testing and security assessment purposes, enabling them to assess the security posture of organizations’ networks and identify potential vulnerabilities that could be exploited by malicious actors.
Read About: Top Best Programming Languages All Time In The World
Limitations of Netcat

Netcat is a command-line utility and lacks a graphical user interface (GUI), which may pose challenges for users accustomed to GUI-based tools. Users may require some familiarity with the command line to utilize Netcat effectively.
While Netcat offers a wide range of functionality related to network connections, it may lack some advanced features found in specialized tools dedicated to specific tasks such as port scanning, packet sniffing, or vulnerability scanning.
Best Practices for Ethical Hacking with Netcat – Best Ethical Hacking Tools
Before using Netcat for network-related activities, users must obtain proper authorization from the relevant stakeholders. This ensures compliance with legal and ethical guidelines and helps prevent unauthorized access to networked systems.
Ethical hackers and network administrators should exercise caution and discretion when using Netcat to avoid causing disruptions or inadvertently disclosing sensitive information. Responsible usage entails respecting the privacy and security of networked systems and adhering to ethical principles at all times.
Read About: Top Best Movies All Time In The World
NetScanTools
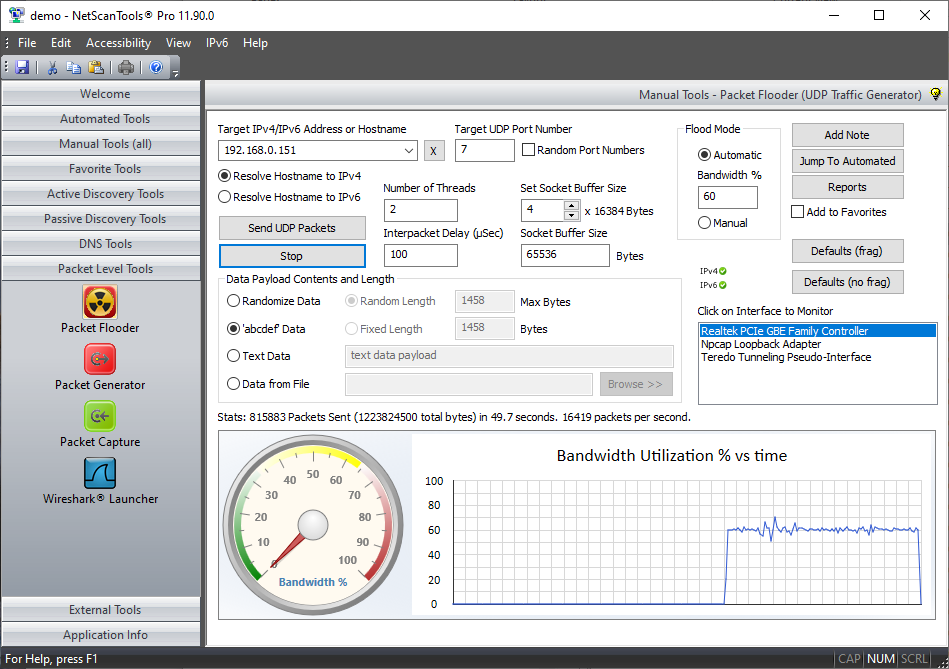
Ethical hacking tools are software applications designed to help cybersecurity professionals assess the security of computer systems, networks, and applications. These tools simulate real-world hacking techniques to identify weaknesses and vulnerabilities that could be exploited by unauthorized individuals.
Importance of Ethical Hacking
With the increasing prevalence of cyber threats, the importance of ethical hacking cannot be overstated. By proactively identifying and addressing security vulnerabilities, ethical hackers help organizations safeguard their sensitive data and protect against cyber attacks.
Overview of NetScanTools
NetScanTools is a comprehensive suite of network security tools developed by Northwest Performance Software, Inc. It is designed to provide network administrators and security professionals with the ability to perform a wide range of network diagnostics, security assessments, and troubleshooting tasks.
Using NetScanTools for Ethical Hacking
One of the primary functions of NetScanTools is network mapping and enumeration. It allows users to discover devices connected to a network, identify open ports, and gather information about network services and protocols.
NetScanTools enables users to conduct port scanning to identify open ports on target systems. This information is crucial for assessing the security posture of a network and identifying potential entry points for attackers.
The Whois lookup feature of NetScanTools provides information about domain registrations, including the owner’s contact details, registration date, and expiration date. This information can be valuable for investigating suspicious domains and identifying potential threats.
NetScanTools offers robust DNS analysis capabilities, allowing users to perform DNS lookups, reverse DNS lookups, and DNS zone transfers. This helps in identifying misconfigured DNS records and potential security vulnerabilities.
NetScanTools in Practice
Several real-world case studies demonstrate the effectiveness of NetScanTools in identifying and mitigating security risks. From uncovering hidden network devices to detecting rogue servers, NetScanTools has proven to be a valuable asset for cybersecurity professionals.
NetScanTools can be used in various scenarios, including network security assessments, incident response, penetration testing, and forensic investigations. Its versatility and ease of use make it a preferred choice for ethical hackers worldwide.
Advantages of NetScanTools
- User-friendly interface
- Comprehensive feature set
- Regular updates and support
- Affordable pricing
- Compatibility with Windows operating system
Limitations and Risks
While NetScanTools offers numerous benefits, it is essential to acknowledge its limitations and potential risks. Like any other hacking tool, NetScanTools should be used responsibly and ethically, ensuring compliance with applicable laws and regulations.
Ethical Considerations in Hacking
Ethical hackers are bound by a code of conduct that emphasizes integrity, professionalism, and respect for privacy. When using tools like NetScanTools, it is crucial to prioritize ethical considerations and adhere to ethical hacking principles.
Read About: Top Best Mobiles All Time In The World
Nessus – Best Ethical Hacking Tools
Ethical hacking tools are software applications designed to help cybersecurity professionals assess the security of computer systems, networks, and applications. These tools simulate real-world hacking techniques to uncover vulnerabilities that could be exploited by malicious actors.
Importance of Ethical Hacking
In today’s digital landscape, where cyber threats are rampant, ethical hacking is essential for organizations to protect their assets and sensitive data. By proactively identifying and addressing security vulnerabilities, ethical hackers help prevent cyber attacks and data breaches.
Overview of Nessus
It is renowned for its comprehensive vulnerability scanning capabilities and extensive database of known vulnerabilities.
Using Nessus for Ethical Hacking
One of the primary functions of Nessus is vulnerability scanning. It automatically scans networks, systems, and applications to identify known vulnerabilities, misconfigurations, and potential security risks.
Nessus enables users to perform configuration audits to ensure compliance with industry standards and best practices. It checks system configurations against predefined policies and benchmarks to identify deviations and security weaknesses.
Nessus includes malware detection capabilities, allowing users to scan for signs of malicious software on networked devices. By detecting malware early, organizations can prevent potential security breaches and data exfiltration.
Nessus in Practice
Numerous case studies illustrate the effectiveness of Nessus in identifying and mitigating security risks. From detecting critical vulnerabilities to improving overall security posture, Nessus has proven to be a valuable asset for organizations of all sizes.
Nessus is utilized in various scenarios, including vulnerability management, compliance auditing, incident response, and penetration testing.
Advantages of Nessus
- Comprehensive vulnerability scanning
- Extensive database of known vulnerabilities
- User-friendly interface
- Flexible deployment options
- Regular updates and support
Limitations and Risks
While Nessus offers numerous benefits, it is essential to acknowledge its limitations and potential risks. False positives, scan inaccuracies, and network disruptions are among the challenges that users may encounter when using Nessus.
Ethical Considerations in Hacking
Ethical hackers using Nessus are bound by a code of conduct that emphasizes integrity, professionalism, and respect for privacy. It is crucial to use Nessus responsibly and ethically, ensuring compliance with relevant laws and regulations.
Read About: Top Best Market All Time In The World
Nmap

Ethical hacking tools encompass a range of software applications designed to assess the security of computer systems, networks, and applications. These tools simulate real-world hacking techniques to uncover vulnerabilities and bolster cybersecurity defenses.
Importance of Ethical Hacking – Best Ethical Hacking Tools
In today’s interconnected world, where cyber threats are rampant, ethical hacking plays a pivotal role in fortifying digital defenses. By proactively identifying and addressing security weaknesses, ethical hackers help organizations safeguard their assets and protect against cyber attacks.
Overview of Nmap
It is renowned for its flexibility, speed, and comprehensive feature set, making it a staple tool for cybersecurity professionals worldwide.
Features of Nmap
Nmap offers a wide array of features, including:
- Network discovery
- Port scanning
- Operating system detection
- Service version detection
- Scriptable interaction with the target
- And much more
Using Nmap for Ethical Hacking
One of the primary functions of Nmap is network discovery. It enables users to identify devices connected to a network, including computers, servers, routers, and IoT devices, providing valuable insights into the network topology.
Nmap facilitates port scanning, allowing users to identify open ports on target systems. By scanning for open ports, ethical hackers can assess the accessibility of network services and identify potential entry points for attackers.
Nmap employs various techniques to detect the operating system running on target systems. This information is valuable for understanding the target environment and tailoring subsequent attacks or security assessments accordingly.
Nmap can also detect the versions of services running on target systems, such as web servers, FTP servers, and database servers. This helps in identifying outdated software versions vulnerable to known exploits.
Nmap in Practice
Numerous case studies demonstrate the effectiveness of Nmap in identifying and mitigating security risks. From detecting misconfigured network devices to uncovering hidden services, Nmap has proven to be a valuable asset for cybersecurity professionals.
Nmap is used in various scenarios, including network reconnaissance, vulnerability assessment, penetration testing, and forensic analysis. Its versatility and reliability make it suitable for organizations across industries, from small businesses to large enterprises.
Advantages of Nmap
- Open-source and free to use
- Comprehensive feature set
- Fast and efficient scanning
- Cross-platform compatibility
- Active community support and regular updates
Limitations and Risks
While Nmap offers numerous benefits, it is essential to consider its limitations and potential risks. False positives, network disruptions, and legal implications are among the challenges that users may encounter when using Nmap.
Ethical Considerations in Hacking
Ethical hackers using Nmap are bound by a code of conduct that emphasizes integrity, professionalism, and respect for privacy. It is crucial to use Nmap responsibly and ethically, ensuring compliance with applicable laws and regulations.
Read About: Top Best Luxurious Hotels All Time In The World
Metasploit – Best Ethical Hacking Tools

Ethical hacking tools are software applications designed to assess the security of computer systems, networks, and applications. These tools simulate real-world hacking techniques to uncover vulnerabilities and strengthen cybersecurity defenses.
Importance of Ethical Hacking
In today’s digital landscape, where cyber threats are ever-evolving, ethical hacking is crucial for organizations to protect their assets and sensitive data. By proactively identifying and addressing security weaknesses, ethical hackers help mitigate the risk of cyber attacks and data breaches.
Overview of Metasploit
Metasploit is a renowned penetration testing framework developed by Rapid7. It provides cybersecurity professionals with a comprehensive set of tools for conducting penetration tests, exploit development, and vulnerability research.
Features of Metasploit
Metasploit offers a wide range of features, including:
- Exploitation
- Post-exploitation
- Payload generation
- Network reconnaissance
- Vulnerability scanning
- And much more
Using Metasploit for Ethical Hacking
One of the primary functions of Metasploit is exploitation. It allows users to exploit known vulnerabilities in target systems to gain unauthorized access or execute arbitrary code. Metasploit includes a vast database of exploits for various operating systems, applications, and network services.
Metasploit facilitates post-exploitation activities, enabling users to maintain access to compromised systems, escalate privileges, and pivot to other network segments. It provides a range of post-exploitation modules for performing tasks such as file manipulation, process management, and credential theft.
Metasploit enables users to generate customized payloads for delivering exploits to target systems. These payloads can be tailored to evade detection mechanisms and achieve specific objectives, such as remote command execution or data exfiltration.
Metasploit in Practice
Numerous case studies highlight the effectiveness of Metasploit in identifying and exploiting security vulnerabilities. From gaining unauthorized access to critical systems to demonstrating the impact of potential cyber attacks, Metasploit has proven to be an invaluable tool for cybersecurity professionals.
Metasploit is utilized in various scenarios, including penetration testing, red team exercises, incident response, and security research. Its flexibility, scalability, and extensibility make it suitable for organizations of all sizes and industries.
Advantages of Metasploit
- Comprehensive penetration testing framework
- Extensive database of exploits and payloads
- User-friendly interface with graphical and command-line interfaces
- Active community support and regular updates
- Integration with other security tools and platforms
Limitations and Risks
While Metasploit offers numerous benefits, it is essential to consider its limitations and potential risks. False positives, unintended consequences, and legal implications are among the challenges that users may encounter when using Metasploit.
Ethical Considerations in Hacking
Ethical hackers using Metasploit are bound by a code of conduct that emphasizes integrity, professionalism, and respect for privacy. It is crucial to use Metasploit responsibly and ethically, ensuring compliance with relevant laws and regulations.
Read About: Top Best Horror Movies All Time In The World





